Identity and Access Management is the first chapter of the Cloud Security 101 rule book. Ensuring that your machine and human identities access only the resources they need to work is even more critical as your cloud environment becomes more complex. But the success of your IAM strategy depends on the strength of your IAM policy.
A worrying 99% of companies have overly permissive IAM policies. By giving your identities more permissions than they need to perform their tasks, you create avoidable security gaps that attackers can use to enter your systems. At a time when cyber attacks can cost businesses billions of dollars, one security gap is one too many.
AWS provides an IAM Policy Simulator to streamline the IAM policy writing process and help you draft more robust policies. However, if you think this service is all you need to create foolproof IAM policies - you might need to think again. In this article, we dive into AWS IAM Policy Simulator and share why this service can prove inadequate for users looking to prioritize usability, scalability, and security.
What is the AWS IAM Policy Simulator?
The AWS IAM Policy Simulator is an online tool that allows you to simulate and test the effectiveness of your IAM policies within your AWS environment. With the simulator, you can verify and fine-tune the permissions granted to different IAM identities. The goal is to ensure that your access controls are correctly configured and in line with your security strategy before you apply the IAM policies to a live environment.
The simulator also supports testing IAM policies using different variables, such as time of day or specific conditions, allowing users to assess the impact of dynamic access controls. There is no denying that AWS IAM Policy Simulator can be a helpful tool to enhance your cloud security posture, but don’t pin all your hopes on it - as we will see below, there are quite a few areas where the simulator falls short.
How the AWS IAM Policy Simulator Works
The tool can be accessed through a web app or command line. It parses the permissions you have written using AWS' IAM JSON policy language and evaluates whether a resource with this policy could perform a given action. Simulator tests do not make actual AWS service requests, so you can experiment freely without changing your environment. Similarly, any policies you change within the simulator will not change in your AWS account.
The app can only test identity-based policies corresponding to users, resources, roles, or user groups. It cannot simulate cross-account users or service control policies. You can simulate different access scenarios by specifying the IAM entities involved, their actions, and the resources they can access. Then, you can define hypothetical situations and evaluate the outcome of your IAM policies.
The simulator provides results on which actions were allowed or denied based on the assessed policies, so you can more easily identify potential security gaps and vulnerabilities and correct them pre-production. Additionally, it will enable you to create and share simulation templates, which you can reuse later.
Why using an IAM Policy Simulator is not enough for cloud security
1. You still need to create your policies
The Policy Simulator can test IAM policies that have already been written. Still, it does not help you draft the policy language or show you the access resources needed to function. The result is trial and error, where you blindly create a policy and tediously test variants until you find an approach that works. While it would be great to test your policies continuously until they are exactly how you want them to be (and fully secure) - this doesn’t work in practice. Engineers are being pulled into various directions and don’t have enough free time to edit thousands of policies manually.
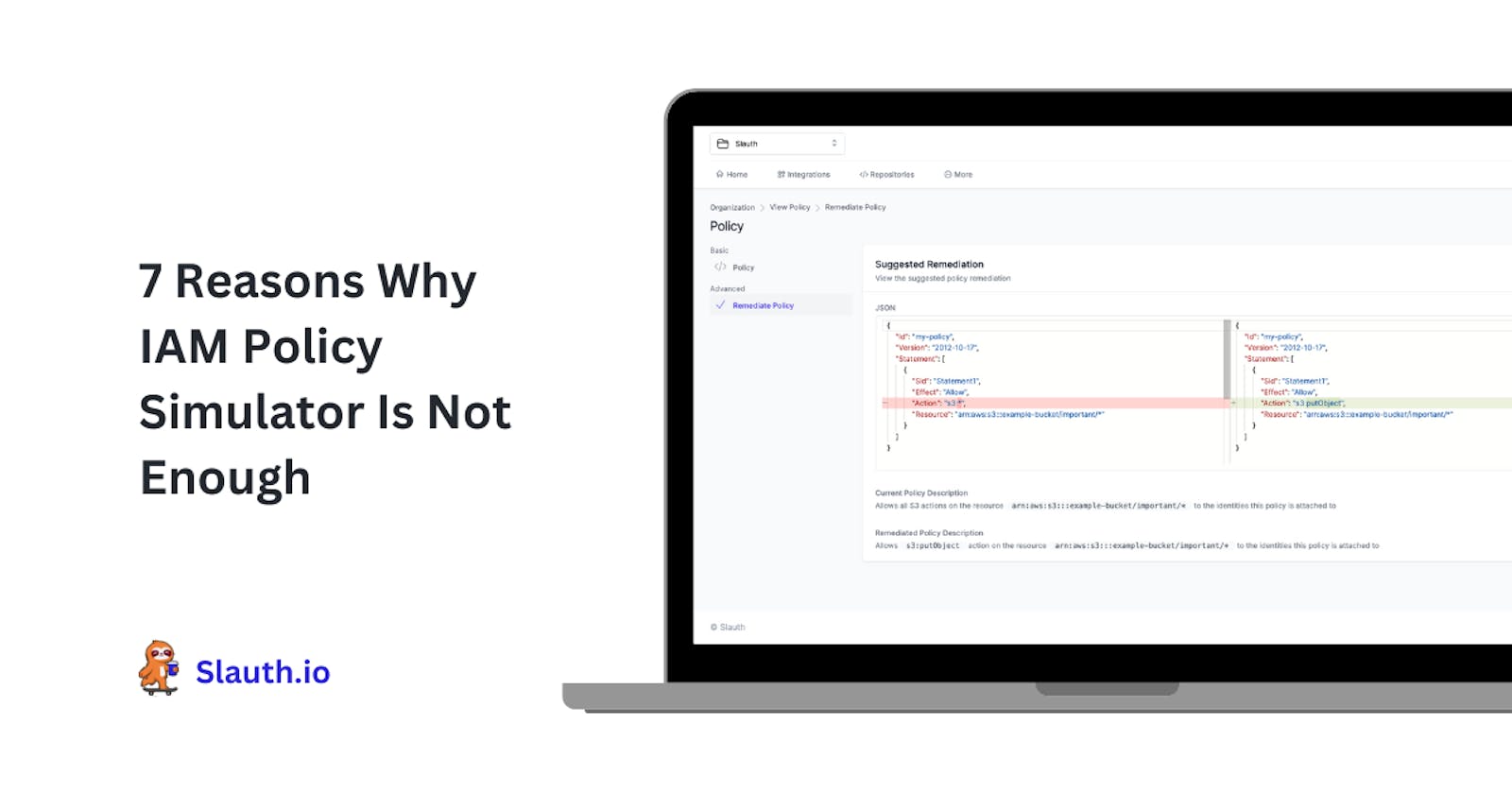
Engineering teams need a way to automate the IAM policy creation process to save precious time and ensure that the policy is strong enough from the get-go, avoiding constant access control updates and security fixes. Slauth.io’s IAM Policy Copilot does just that and much more. It monitors the activity of your machine-based identities to create policies that match their behavior, giving them access to only the necessary resources. Plus, no more building policies manually from scratch.
2. Your test results may differ from your live AWS environment
As mentioned prominently in AWS' documentation, "the policy simulator results can differ from your live AWS environment." Even after testing your policy in the simulator, you can’t take the outcomes as definitive and must test it again in your live environment. This adds another step to the policy development process.
3. It is a very manual process
Drafting IAM policies using only the Policy Simulator is manual and time-consuming. As your organization grows, the interconnections between all your resources, workloads, and machine identities become ever more complex, creating an unsustainable web of conflicting policies. Continuously supporting, maintaining, and reviewing IAM policies can become arduous.
Slauth.io's IAM Policy Copilot automatically builds your policies as resources are added and deployed. It also supports automated end-to-end tests, removing the need for manual intervention while ensuring suitably restrictive permissions.
4. Updates will be needed over time
Policy definitions are static, so they will need continuous updating to reflect the dynamic nature of your resources. Even the best, most secure policy will need edits and yet more tests as users move onto different teams, new projects are spun up, and policies are revised by management. Every change translates to more policy drafting, more testing with the Policy Simulator, and more places where mistakes can be made.
5. It doesn't monitor machine activity
By design, the policy simulator is limited in scope. It doesn't perform ongoing checks on policies in production environments, log user events, or check for unusual activity. Continuous monitoring is essential when creating and maintaining a robust IAM estate, and you can’t just focus on monitoring human identities either.
With enterprises having, on average, 250 thousand machine identities (a good part of which is in the cloud infrastructure), ensuring the proper access controls to machine identities is just as essential. It’s easy to forget machine identities when dealing with actual users (human identities), but the breadth of machine identities connected to your cloud is significant. Below are some examples of machines whose access you may need to manage:
You can augment AWS's functionality with tools like Slauth.io, which provides more detailed logs of user activity and detects IAM changes automatically for early anomaly detection. Plus, our robust auditing and reporting features enable you to prove compliance with key regulations such as HIPAA and GDPR.
6. It doesn't provide recommendations
AWS IAM Policy Simulator only provides a simple binary result for a given action - "allowed" or "denied." There are no recommendations about superfluous permissions granted, short scope, or security best practices. This can make the process of finding the optimal policy somewhat burdensome.
7. It doesn't consider the Least Privilege
Least Privilege is the principle that code should run with the minimum permissions required to function. The approach is widely considered a security best practice because it reduces the possible access points for cyber attacks and should be what every cloud stack strives to achieve.
Finding the least privilege required is a difficult balance, and privilege creep (where, over time, users and resources are given more permissions than they need) is standard. The Policy Simulator tool cannot tell you the least privilege required for a resource or actively fight against privilege creep.
Slauth.io dynamically creates least-privilege policies for you based on real-time API log activity. This can drastically reduce the possible vectors for attack by closing off unnecessary privileges and ensuring that resources do not have more access than they need.
What can I do to be more secure?
IAM Policy Simulator is an invaluable tool to strengthen your IAM policies. However, as we saw in this article, it can be unscalable, static, and limited in utility when used alone. Not only can it lead to security gaps, but it also requires a lot of extra manual work from your team. Engineers already have too much on their plate, so they need tools to save as much time as possible while keeping their cloud secure.
If you want to learn how Slauth.io can improve your IAM cloud security, join our waiting list!